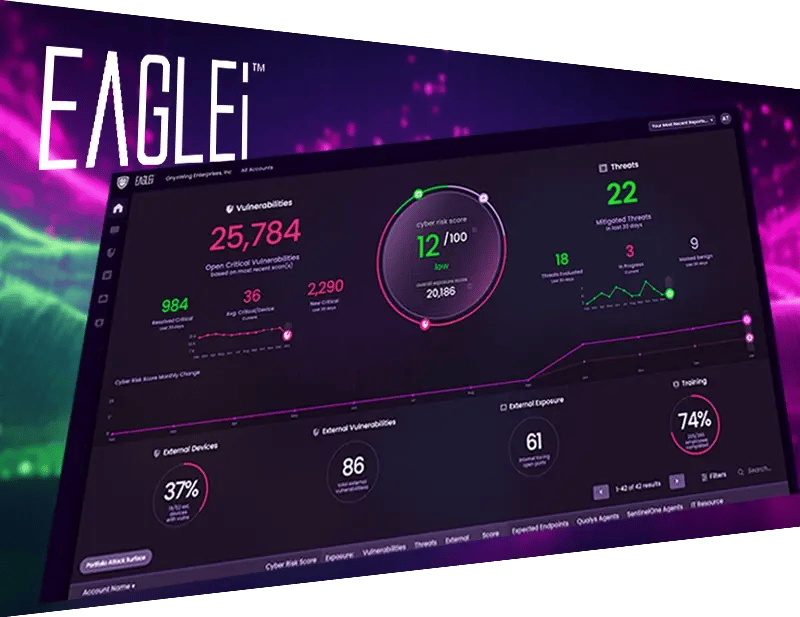
EAGLEi: Your Cyber Guardian
Unleash the power of EAGLEi — your ultimate cyber asset attack surface management solution — and reduce your risk of cyberattacks by up to 90%. Trusted by thousands of businesses, securing over 50,000 computers.

Empowering Autonomous Remediation
EAGLEi’s powerful autonomous remediation capabilities handle up to 70% of system vulnerabilities automatically, empowering your IT team to focus on strategic initiatives and critical tasks. While EAGLEi streamlines the process, it works hand in hand with your team, creating a strong security partnership for your organization.
Cyber Risk Management Features of EAGLEi
Enhance your cybersecurity posture with EAGLEi’s comprehensive suite of tools. From risk detection to proactive remediation, EAGLEi equips you with powerful features for effective cyber risk management.




Testimonials
“Black Talon helps bring your vulnerabilities to light while providing solutions and advice. They have helped us navigate through our vulnerabilities with the help of our IT company without limiting our capabilities.”
Laurissa Ramirez | Guyette Facial & Oral Surgery Center
“With the significant costs and hardships associated with a breach, my feeling is that this is no longer something that we should be considering, it is a must have.”
Dr. Bart Silverman | BWS Oral and Maxillofacial Surgery
“Your IT company’s job is to keep your systems up and running on a daily basis, not cybersecurity. Black Talon will work with your IT company, as a team, to find and close vulnerabilities in your network.”
Dr. Gary Orentlicher | New York Oral, Maxillofacial, and Implant Surgery
Why Choose EAGLEi?
Our solution goes beyond typical cyber software tools. Backed by a dedicated team of security experts, EAGLEi safeguards your network 24/7. Helping you achieve and maintain compliance while providing you with unrivaled protection, we are your steadfast partner in cybersecurity.