Multi-Layered Cyber Prevention
Combat cyberthreats with our expansive suite of services. We go beyond data breach prevention, offering specialized awareness training as an integral part of our full range of solutions to fortify your business’s security.
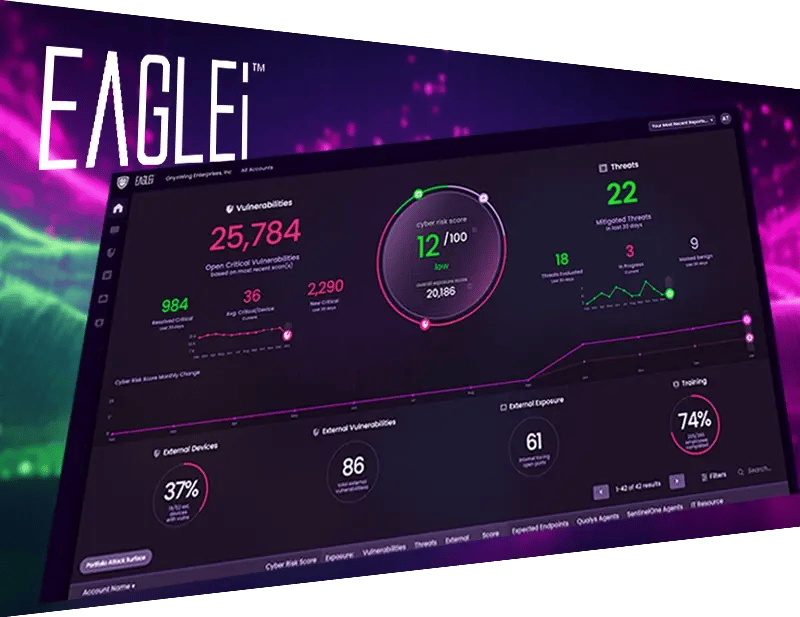
Full Visibility and Proactive Management
With EAGLEi, gain full visibility into potential cyberthreats through AI-powered proactive threat detection and response. Our platform constantly learns and evolves, enabling it to fight back against emerging attacks, ensuring robust security for your business.

Empower Your First Line of Defense
Empower your employees to become your organization’s first line of defense against cyberthreats. Our comprehensive training programs educate and equip your team with the knowledge and skills they need to identify, respond to, and mitigate risks effectively. Strengthen your cybersecurity posture and ensure compliance with security laws through specialized training with both offensive and defensive strategies.

Complete Cyber Solutions — Going Beyond Data Breach Prevention
Protect your business with our extensive toolkit of services. We offer a holistic approach to cybersecurity, combining advanced technologies and expert strategies to safeguard your critical assets.








Testimonials
“Black Talon has been an invaluable partner, ensuring our practice's cybersecurity and HIPAA compliance. Thank you for your expertise and dedication!”
Lynn Howard | Practice Administrator, Summit Oral & Maxillofacial Surgery
“Thanks to Jules and Black Talon Security, our employees received comprehensive HIPAA training that truly hit home. We're confident in our compliance.”
Courtney Dietrich | Practice Manager, Dietrich Orthodontics
“The challenge is that robust security is something not handled by our IT companies. The answer is to utilize a 3rd party company who can implement a multifaceted solution to help minimize the chances of an attack.”
Dr. Michael T. Dachowski | Pennsylvania Dental Implant & Oral Surgery Associates

